Two-factor authentication benefits extend beyond simple security measures. This guide delves into the multifaceted advantages of implementing two-factor authentication, exploring its impact on security, user protection, account recovery, accessibility, cost-effectiveness, compliance, integration, and future trends. From enhanced security protocols to improved user experience, this detailed analysis reveals the crucial role of two-factor authentication in today’s digital landscape.
The core benefits of two-factor authentication lie in its ability to create a layered defense against unauthorized access. By requiring multiple verification steps, it significantly reduces the risk of account breaches and protects sensitive information. This approach not only safeguards individual accounts but also strengthens overall cybersecurity posture for businesses and organizations.
Enhanced Security
Two-factor authentication (2FA) significantly bolsters security protocols by adding an extra layer of verification beyond a simple username and password. This crucial step adds an extra layer of protection, making it considerably harder for unauthorized individuals to access sensitive accounts and data.Implementing 2FA substantially increases the difficulty for attackers to gain unauthorized access. This enhancement is achieved by requiring users to present two distinct forms of identification.
This approach is a fundamental shift from single-factor authentication, where only one form of identification is needed.
Single-Factor vs. Multi-Factor Authentication, Two-factor authentication benefits
Single-factor authentication relies solely on a username and password. This method is vulnerable to various attack vectors, such as password breaches and phishing scams. In contrast, multi-factor authentication, exemplified by 2FA, incorporates an additional verification step, making it much more resistant to unauthorized access attempts.
Common Security Breaches Prevented by 2FA
Two-factor authentication effectively mitigates numerous security threats. For instance, it prevents credential stuffing attacks, where attackers use stolen credentials to access multiple accounts. Furthermore, 2FA can thwart phishing attempts by requiring a second verification step, which attackers typically cannot replicate. Additionally, 2FA is a strong defense against brute-force attacks, where attackers repeatedly try different password combinations.
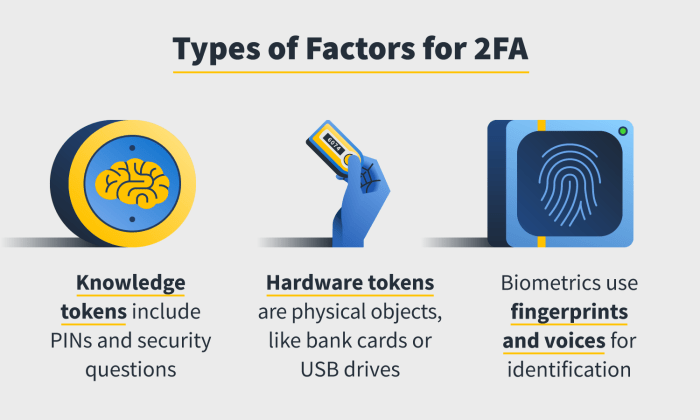
Types of Authentication Methods in 2FA
Various methods are used for the second factor in 2FA. These methods are designed to enhance security and provide diverse user experiences.
- SMS-based authentication utilizes text messages to send a verification code to the user’s phone number. This method is widely available and relatively easy to implement.
- Authenticator apps, such as Google Authenticator or Authy, generate time-based one-time passwords (TOTPs). These apps provide a more secure alternative to SMS-based authentication.
- Hardware tokens are physical devices that generate unique codes. These tokens offer a high level of security but often have a higher implementation cost.
- Email-based authentication sends a verification code to the user’s email address. This method is less secure than authenticator apps or hardware tokens, as email accounts can be compromised.
Effectiveness and Usability Comparison of 2FA Methods
The following table provides a comparative analysis of different 2FA methods, considering security level, user friendliness, and implementation cost.
Two-factor authentication is crucial for online security. It adds an extra layer of protection, making it significantly harder for unauthorized access. This is particularly important when considering sensitive data like those needed for online transactions. A strong security posture, like the benefits of two-factor authentication, also relates to personal well-being. For example, safeguarding your digital life is similar to maintaining a healthy routine like caring for your skin.
Caring skin requires consistent care, just as robust online security necessitates the use of two-factor authentication. Ultimately, both contribute to a more secure and healthy existence.
| Method | Security Level | User Friendliness | Implementation Cost |
|---|---|---|---|
| SMS-based authentication | Moderate | High | Low |
| Authenticator apps | High | High | Low |
| Hardware tokens | Very High | Moderate | High |
| Email-based authentication | Low | Moderate | Low |
Integration with Existing Systems
Integrating two-factor authentication (2FA) seamlessly into existing systems is crucial for maximizing its security benefits without disrupting operations. This involves careful planning and consideration of the current infrastructure and workflows. A well-integrated 2FA solution should minimize friction for users while significantly bolstering overall security posture.
Ease of Integration
FA integration with existing systems varies depending on the complexity of the system and the chosen 2FA provider. Modern 2FA solutions are designed with APIs and SDKs that facilitate easy integration with various platforms. This often involves minimal code changes and configuration adjustments to existing applications. Providers frequently offer comprehensive documentation and support resources to guide developers through the integration process.
Examples of Integrations
Numerous platforms and services have successfully integrated 2FA. Examples include: email platforms integrating 2FA via SMS or authenticator apps; cloud storage solutions employing 2FA for access control; and online banking systems utilizing 2FA to secure user accounts. These examples demonstrate the versatility and applicability of 2FA across different sectors.
Technical Requirements
Several technical factors need consideration during the integration process. These include API access and authentication mechanisms, user account management within the existing system, and compatibility with the chosen 2FA provider. The provider’s documentation should be carefully reviewed to ensure that all technical requirements are met and the integration is secure.
Benefits of Seamless Integration
Seamless integration leads to a positive user experience. Users can access applications and services without encountering complex or cumbersome 2FA procedures. This fosters user adoption and enhances overall security without impacting user productivity. The integration also allows for better security monitoring and management, enabling timely responses to potential security threats.
Compatibility Table
| Authentication Provider | Supported Platforms | API Integrations |
|---|---|---|
| Google Authenticator | Web applications, mobile apps, desktop applications | REST APIs, SDKs for various programming languages |
| Authy | Mobile apps, web applications, APIs for various programming languages | REST APIs, SDKs for various programming languages |
| Duo Security | Mobile apps, web applications, APIs for various programming languages | REST APIs, SDKs for various programming languages |
| Microsoft Authenticator | Web applications, mobile apps, desktop applications | REST APIs, SDKs for various programming languages |
Note: This table is a simplified representation and may not include all possible integrations. Specific platforms and API capabilities can vary based on individual provider configurations.
Implementation Strategies
Implementing two-factor authentication (2FA) in a business setting requires a well-defined strategy that considers the unique needs and infrastructure of the organization. This process encompasses various stages, from initial planning to ongoing maintenance, ensuring a smooth transition and maximum security benefits. Careful consideration must be given to user training and communication to maximize adoption and minimize friction.A comprehensive 2FA implementation strategy should address the entire user lifecycle, from onboarding to ongoing support.
This proactive approach minimizes disruptions to business operations and maximizes user adoption.
Planning and Preparation
Thorough planning is critical for a successful 2FA implementation. This phase involves identifying the specific needs of the organization, evaluating existing systems, and selecting the appropriate 2FA solution. A detailed assessment of the current infrastructure, user base, and security policies is essential. Understanding the technological capabilities and limitations of the existing systems is vital to ensure a smooth integration of the 2FA solution.
Selecting a 2FA Solution
Several factors influence the selection of a suitable 2FA solution. These include the company’s security requirements, budgetary constraints, existing infrastructure, and anticipated user volume. A thorough evaluation of different providers, considering their security certifications, technical support, and scalability, is essential. Evaluating the solution’s compatibility with existing systems is also critical to minimize disruption during implementation. Open communication with the chosen provider is vital throughout the implementation process.
User Training and Communication
Effective user training is crucial for a successful 2FA implementation. This involves providing clear and concise instructions on how to use the new authentication method. Detailed documentation, step-by-step guides, and interactive tutorials are essential for ensuring a smooth transition. Communicating the benefits of 2FA to employees is vital. Emphasize that the added layer of security protects sensitive data and company assets.
Clear communication about the reasons behind the implementation and the anticipated benefits fosters employee cooperation and acceptance.
Two-factor authentication significantly boosts security, making accounts virtually impenetrable. Think of it like adding an extra layer of protection, similar to the luxurious hydration offered by la mer moisturizing cream , which locks in moisture and shields your skin. This extra precaution is crucial for safeguarding sensitive data, ensuring peace of mind.
Phased Implementation
A phased approach to implementation is often beneficial. This allows for a gradual rollout of the new system, minimizing potential disruptions to business operations. It also provides an opportunity for testing and troubleshooting in a controlled environment before a full-scale deployment. This approach permits for feedback and adjustments based on initial user experience.
Ongoing Maintenance and Support
Ongoing maintenance and support are crucial for a long-term successful 2FA implementation. This includes regular updates to the solution, monitoring for vulnerabilities, and providing timely assistance to users. A dedicated support team should be available to answer questions and resolve any issues. A comprehensive support strategy ensures continued functionality and security of the implemented 2FA solution.
Future Trends and Developments

Two-factor authentication (2FA) is constantly evolving to address emerging security threats and user expectations. This dynamic landscape presents both challenges and opportunities for businesses and individuals seeking robust security measures. The future of 2FA will be characterized by increased sophistication, integration with existing systems, and a greater emphasis on user experience.The future of 2FA is shaped by several emerging technologies and trends.
These trends will significantly impact how 2FA is implemented and utilized in the years to come. The adoption of more advanced authentication methods, coupled with the growing need for seamless user experiences, is driving this evolution.
Forecasted Developments in 2FA Technology
Future advancements in 2FA technology are likely to incorporate biometrics, behavioral analytics, and artificial intelligence (AI) to enhance security and user experience. Biometric authentication methods, like facial recognition or fingerprint scanning, will become more integrated and prevalent, particularly for high-security environments. These methods offer a high level of security, reducing the risk of unauthorized access.
Emerging Technologies Impacting 2FA
Several emerging technologies significantly influence 2FA’s future direction. The increasing ubiquity of mobile devices, the evolution of the internet of things (IoT), and the rise of cloud computing are key factors impacting the evolution of 2FA. 2FA is adapting to accommodate these trends, with greater emphasis on user convenience and seamless integration across various platforms.
Adapting 2FA to New Security Threats
Two-factor authentication is continuously adapting to new security threats. Phishing and social engineering attacks, as well as advanced persistent threats (APTs), require 2FA systems to become more resilient. Advanced authentication methods that leverage machine learning and behavioral analytics will be critical in detecting and preventing fraudulent activities. This adaptability is crucial for maintaining a high level of security in a constantly evolving threat landscape.
Future Challenges and Opportunities in 2FA
While 2FA presents numerous opportunities, future challenges exist. Ensuring the security and privacy of user data associated with 2FA systems is paramount. Also, maintaining user trust and mitigating the complexity of multi-factor authentication procedures is essential. The development of standardized 2FA protocols and improved interoperability will be important for seamless integration across various platforms. Further opportunities exist in the integration of 2FA with emerging technologies such as blockchain.
Evolution and Improvement of 2FA
FA will continue to evolve and improve over time, incorporating innovative technologies and addressing new security concerns. The use of hardware tokens, alongside mobile-based authentication, is expected to increase, offering users greater control and flexibility. This evolution will also involve a more user-friendly design and seamless integration with existing systems. Examples of this include the integration of 2FA into social media platforms or banking apps.
Concluding Remarks
In conclusion, implementing two-factor authentication offers substantial advantages in terms of security, user protection, and cost-effectiveness. By reinforcing security protocols, safeguarding user accounts, and simplifying recovery procedures, two-factor authentication empowers individuals and organizations to navigate the digital realm with greater confidence. The guide presented a detailed overview of this crucial security measure, highlighting its versatile applications and future potential.
Adopting two-factor authentication is a proactive step towards a safer and more secure digital future.
Query Resolution: Two-factor Authentication Benefits
What are the different types of authentication methods used in two-factor authentication?
Common methods include SMS text messages, email verification, authenticator apps (like Google Authenticator), and hardware tokens. The best method depends on individual needs and security requirements.
How does two-factor authentication simplify account recovery?
Two-factor authentication typically requires more than one verification method during the recovery process. This adds an extra layer of security, making it harder for unauthorized individuals to access accounts.
What are some examples of organizations that have successfully implemented two-factor authentication and reduced security incidents?
Many large companies and online services have successfully integrated two-factor authentication, leading to a significant reduction in security breaches. Publicly available case studies often highlight these positive outcomes.
What are the potential future challenges related to two-factor authentication?
Future challenges may include the increasing sophistication of cyberattacks and the need for two-factor authentication to adapt to emerging threats and technologies.





